27/05/2024
CTI
Elections: a year of threats – Episode 4
The fourth episode of our elections series is out!
The U.S. presidential elections are exciting affairs, with the results having an impact far beyond the 51 states. In the face of fragile geopolitical equilibrium and stalemated armed conflicts, every passing day promises an increase in cyber threats. We take this opportunity to review the inseparable links between cyberspace and geopolitics. Analysing the attack vectors of the US voting ecosystem highlights the way in which a state or group can act against the heart of democracy.
All shoots are fired.
The threat landscape cannot be understood without understanding the geopolitical landscape. This is even more true during election s, especially a major one like in November.
Like in 2020, the 2024 elections promise to be far from boring. National and international issues are intertwined in what seems to be a drama show. Americans will vote with mostly domestic policy in mind. However, foreign policy must be considered when looking at the possibility of interference.
Not to change China, Russia and Iran have been identified by the United States as the three majors foreign cyberthreats. Those countries are conducting hybrid cyber-operations (both cyber-attacks, interference, and disinformation). The election context is the perfect platform for opportunistic and/or targeted actions from either cybercriminals or state actors. And those actions are in direct connection to the following geopolitical issues.

Ukraine
As a revival of Russian operations on the front is expected to happen this summer, the Biden administration hasn’t been clear on its position regarding the war in Ukraine. The gap between the talks condemning Putin’s actions and the actual support is another evidence of America’s disengagement in Europe.
The Trump administration, as in 2016, can be expected to follow the vision of their leader “In fact, I would encourage to do whatever the hell they want”[1] . Talking about Russia, Trump has always processed – and he isn’t the only one – that some NATO members (mostly European) don’t meet the defence budget required. That recurrent topic puts pressure on discussions of common actions regularly. Russia’s interference is expected to reinforce this rhetoric and campaigns from Russian- speaking threat actors has been discovered. The objective is to manipulate opinions to lessen the support of Ukraine. Propagate this rhetoric is encouraging parts of the population that already share the opinion that Europe should deal with Russia which will serve the Kremlin political agenda. By pushing for Trump’s victory, Moscow wants to ensure that no American sanctions will be applied when there is another salvo of attacks.

Made in America
Behind this marketing argument lies true political and economic challenges. Seeing China as their great foe, the U.S. have been trying to counterbalance Chinese exports rate to promote their own national production lines and restore the economy. The trade policies put in application impacting Chinese and European industries have put a strain on the world economy. Part of the “made in America” concept and under the Inflation Reduction Act, both Trump’s and Biden’s administrations had ambitions to protect the U.S. national security and maintain their leadership in key advanced technologies and market shares. This is a major issue in this election as part of the population is blaming the actual President for trade policies crippling the U.S. national economy. China could be using that opportunity to sway opinions via diasporas to influence American trade policies in the long run by encouraging candidates less opposed to economics exchanges with China.

Gaza
The Middle East is again at the heart of geopolitical tensions. The Israeli-Hamas war is testing the relations between the United States and Israel, its long-standing ally. The Abraham agreements signed in September 2020 by Israel, Bahrain and the United Arab Emirates were intended to define the terms of a de-escalation in the region. The recognition of Israel as a regional state, which is still scattered, was intended to contain Iran’s ambitions. Iran is a key player in the region and the war is an opportunity for Teheran to affirm its regional leadership in the Middle East. By delaying the cease fire advocated by the United Nations and potentially supporting Israel with troops on the ground, the United States are facing, like Israel, threats of retaliation from the Iranian government. Iran could respond to military interventions and geopolitical sanctions by using the United States’ election platforms to conduct disruption operations and demonstrates its power.

Trust in our democratic system
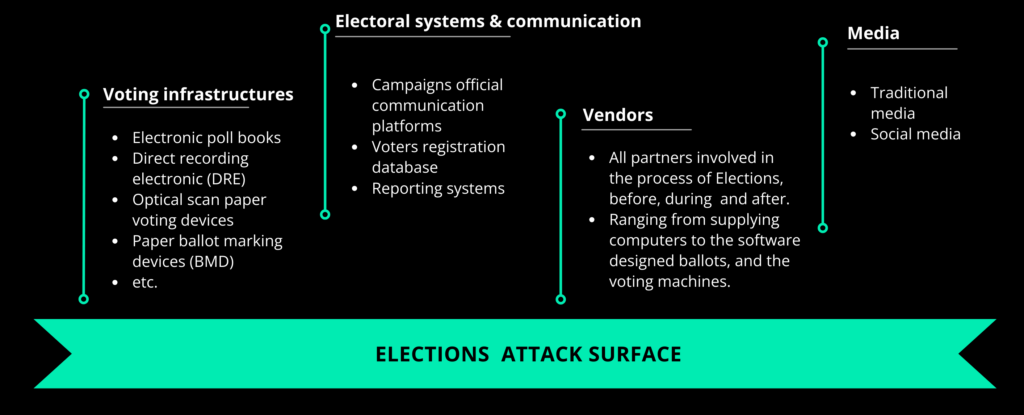
The fear is that looking to either influence, undermine or disrupt, threat actors and cybercriminals will target the election. To understand what that means we should consider the whole voting ecosystem as it’s composed of multiple devices and third parties (shown under).
Operations les by the United States since the 2000s
More than ever, media and authorities are warning from the risk of cyber-attacks during the US elections. Voting machines have been under the scrutiny of cybersecurity experts as vendors were not open to let them look under the hood of their vulnerable business. Not all is due to suspicion or lack of interest for security but also to the thinking mode of industries.
It is true, like most operation infrastructure, cybersecurity wasn’t the priority in the voting devices industry and teemed with exploitable vulnerabilities. Like the energy sector taken as an example in our latest Threat Landscape, the same technical constraints are identified in the voting industry. That makes it difficult to update and patch devices for well-known vulnerabilities.
Experts have come across well-known vulnerabilities:
- Weak password stored in clear;
- Security features deactivated allowing the e-pool book to load unsigned code from any source;
- Lack of physical security that allows threat actors to become root and access the unencrypted drive;
- Lack of patch management with systems not updated.
CISA has advertised on vulnerabilities in the Dominion Voting Systems in 2022. It is important to note that to this date, no successful attacks have been registered during any US elections using this vulnerability.
The DefCon report is eloquent on the vulnerabilities found but also on possible attacks. For most attacks, a physical presence would be required to compromise the systems and remote exploits isn’t an easy task. Not saying it isn’t possible, but we must look at the threat actors that would have the means and the motivation to conduct such operations.
However, we must also keep in mind that sometimes saying that it can be done is enough to manipulate. The overbearing talk about the vulnerability of our core democratic system is as dangerous as a real attack. It creates a sense of mistrust in the population, that impact the election result.
Next to vulnerability exploits on voting devices, other threats have been identified. Those aren’t new but in the context of elections they must be taken into counting.

Operations les by the United States since the 2000s
- Distributed Denial of service attacks
Disrupt means to interrupt or alter a system, a process, or an event. Regarding the elections cycle, disruption occurring at key moments in elections’ related services could impact the ability for voters to register, access critical information, etc.
- Social engineering
Elections, like the Paris Olympics, represent an opportunity to conduct spear-phishing campaigns. Those attacks can be opportunistic (mostly fraud) or targeted for example on official staff to retrieve authentication information to be used in later attacks.
- Information operation
Undermine or influence could be transpired through propaganda, disinformation and/or misinformation campaigns. Becoming a common threat, compromised social media, or valid accounts are used to discredit, manipulate opinions, or dispute election integrity and results. Generative IA is another layer to maximise the audience reach.
Information operations are mostly conducted by state actors. Even though they are using similar means of information manipulation, the way they are using them can diverge depending on those motivations.
Information operations are mostly motivated by influencing and undermining objectives. Often used interchangeably, there is a nuance to those terms. Undermine means to weaken a process or an authority gradually, often through indirect means. Influence means to cause a change in behaviour, belief, or opinion.

Conclusion
No doubt that American authorities and cybersecurity experts will increase their monitoring until November 6th and for some time after that. Other countries will likely do the same as cyberthreats don’t know borders. They will watch for not only cyber-attacks and warning signs but also the development of the conflicts undergoing and diplomatic relations.
The Voting Village launched in 2017 has shown that the collaboration for better and more secure elections is possible in the United States. Progress in patch management and implementation of the security in depth approach in the manufacturing of those devices are essential.
In the long run, the tangible impact is that democracies are put in doubt because the focus is diverted from actual issues to one core matter: can our democratic system still be trusted?

References
- CNN Politics. 2024. https://edition.cnn.com/2024/02/10/politics/trump-russia-nato/index.html
- Global Government Forum. 2024. https://www.globalgovernmentforum.com/a-subtle-opponent-chinas-influence-operations/
- The Intercept. 2024. https://theintercept.com/2024/03/06/homeland-security-us-elections/
- Congress Gov. 2024. https://www.congress.gov/event/116th-congress/house-event/LC65449/text
- CBS News. 2024. https://www.cbsnews.com/news/russia-iran-china-likely-to-engage-in-new-election-interference-efforts-microsoft-analysis-finds/
- Dark Reading. 2024. https://www.darkreading.com/ics-ot-security/hackers-let-loose-voting-gear-us-election-season
- Dark Reading. 2024.https://www.darkreading.com/cyber-risk/how-can-we-make-election-technology-secure-
- Dark Reading. 2024. https://www.darkreading.com/threat-intelligence/foreign-influence-operations-gearing-up-for-us-election
- Homeland Threat Assessment. 2024. https://www.dhs.gov/sites/default/files/2023-09/23_0913_ia_23-333-ia_u_homeland-threat-assessment-2024_508C_V6_13Sep23.pdf
- HackerOne. 2024. https://www.hackerone.com/ethical-hacker/election-security
- Chatam House. 2024. https://www.chathamhouse.org/2024/03/how-foreign-policy-might-impact-outcome-us-election
- DEF CON 27 Voting Machine Hacking Village. 2024. https://harris.uchicago.edu/files/def_con_27_voting_village_report.pdf
- Iran International. 2024. https://www.iranintl.com/en/202402238236
- Wired. 2024. https://www.wired.com/story/voting-machine-makers-hackers-ess/
- Wired. 2024. https://www.wired.com/story/voting-machine-vulnerabilities-defcon-voting-village/
- Security Affairs. 2024. https://securityaffairs.com/108135/cyber-warfare-2/china-russia-iran-target-us-election.html
- BAE systems. 2024. https://www.baesystems.com/en/digital/blog/the-cyber-impact-on-elections-safeguarding-democracy-in-2024
- Belfer Center. 2024. https://www.belfercenter.org/publication/state-and-local-election-cybersecurity-playbook
- The Diplomat. 2024. https://thediplomat.com/2024/04/us-and-europe-2-different-approaches-to-restricting-chinese-evs/
- CISA. 2024. https://www.cisa.gov/news-events/ics-advisories/icsa-22-154-01









