02/04/2024
CTI
Elections: a year of threats – Episode 1
2024 is the year of elections. But how does it impact the threat landscape?
Almond would like to share a new series to keep track of this year’s threats.
Elections are perfect set ups for states and non-states actors to influence, disrupt, gain power, and attempt to impose their view on the geopolitical landscape.
In our 5 episodes series, we will explore the main cyber and political issues surrounding that crucial time in history.
The first episode is an introduction to this 2024 election marathon.

Introduction to this election series
Every media and government have already said it: 2024 is the year of elections.
A major part of the world population will go to the polls and it’s interesting how that fact brings to light governments’ worst fears. “Year of elections” is revealing a nest of questions relating to democracy and security. In the context of great geopolitical tensions, elections are more crucial to maintain the international order and opportunities to turn the tides.
Those issues are even clearer when we overlap the election map and all hot spots ready to burst. Understanding how conflicts can be used during that “super year” is understanding how easily results could be swayed from one or another influential country.
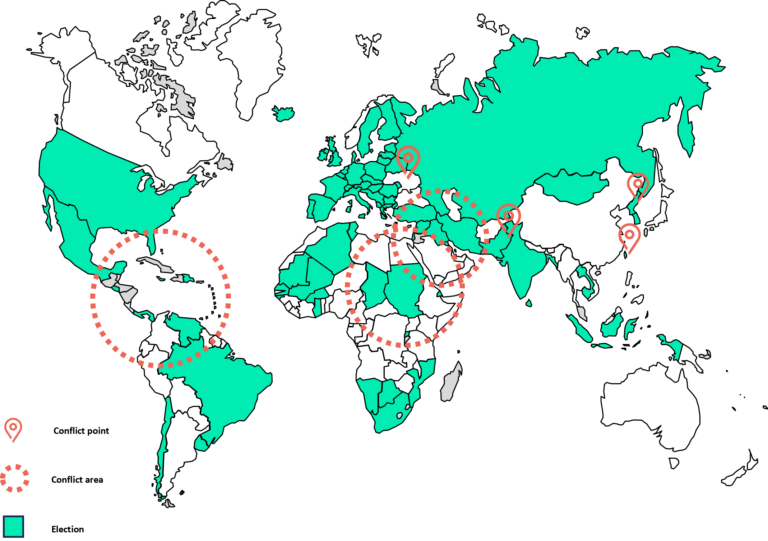
Before and during this elections’ season, governments fear three main threats: interference, disinformation, and cyber threats.
Major risks are associated with those threats :
Interference is the attempt to influence the election to favour candidates who may serve another state’s interests. Election results can then be questioned.
Disruption of the information flow to discredit and polarise opinions is a real threat to democracy. Disinformation is a popular and powerful form of propaganda used to obtain economic or political gain, particularly useful during an election.
If elections don’t usually bring new types of cyber threats but that period increases the risk of being targeted by either states or non-states actors. They use the political chaos to conduct diverse known malicious actions ranging from opportunistic to targeted operations.

Behind election meddling
Strong from the previous elections’ interference, governments and institutions are more and more focus to highlight and counteract foreign practices of meddling. Those practices can have pivotal impacts in a country’s sovereignty and on the population trust in authorities.
If interference is a common practice for countries all over the world, methods differ depending on the culture and objectives. The following three examples are the main types of interference.
Aggressive stance
Countries like Russia have adopted an aggressive approach to propagate their influence, especially in Europe. Using visible practices like disinformation on social media, originated from the early propaganda methods. Their actions have major impacts on elections process and are more covered than other types of interference. Private entities can engage in disinformation as well.
Underground methods
Interference can also be more subtle with governments working in the shadows. Countries having diasporas all over the world can be used as opinion relays. This method is used by China for example, but also Israel, India, etc. They can also implant key people in influential institutions or companies to work from the inside and change slowly strategies and decisions in their sponsor favour.
In the name of democracy
European countries and the United States have been accused of meddling in other states elections for decades. Usually, those accusations come from Eastern and “in development” countries. From those states point of view, “Occidental countries” by trying to promote their view of the world and encourage a democratic system are interfering in local elections. Before 2000, the US were notably known for their actions in other countries to shift the political landscape hiding economic and power grabbing under democratic pretences.










